Posts
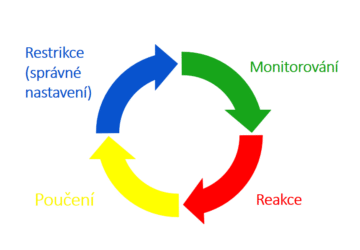
My practical insight into IT security and security life cycle. Everyone deals with restrictions, but what about monitoring, reactions, and lessons learned?
How to Hack a Computer in Seconds or Bash Bunny and Packet Squirrel Attacks
Play how to hack computer videos. I have tested hacking gadgets - Bash Bunny and Packet Squirrel. Everyone can hack, you just need to be interested and have free time!
Network Security: Tier Model and PAW
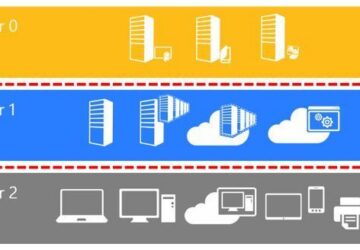
As a network administrator, we have access to all of our customer data. That is why I put a lot of effort into security. Learn about Tier model and PAW.
Password Management 2: We Have Installed Remote Desktop Manager
The new password management system, Remote Desktop Manager, allows us to do things faster and more complexly. Learn about our RDM experience.
How Our Tech Support Operates
The technical support of other companies has become the target of several of my articles. That's why I have decided to describe how our tech support operates. To help you evaluate us.
Non-existent Technical Support: One-Man Show as a Business
Technical support problems will most likely never end. This time, we have encountered a company that is basically a one-man show. And their technical support is just like that.
Monitoring System: What Can We Do
The monitoring system is our "most productive" employee that we have trained to meet our needs. What is it composed of? And what can it do?
Password Management
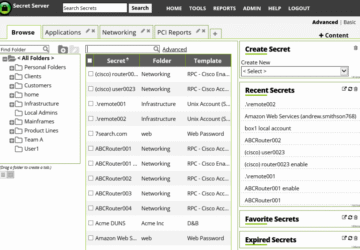
How we handle our customers' passwords. A couple of funny stories from life. And why you should ask your IT guy how he stores your passwords.
Monitoring System: How I Found Out We Need It
How I found out that I need a monitoring system as a network administrator. Or how I stopped working hard and tried to do it smart.
Hacking Gadgets: Hak5 Packet Squirrel
Hak5 Packet Squirrel is another hacking gadget I have tested. What Packet Squirrel can do, where did I buy it and what do I use it for?
Hacking Gadgets: Hak5 Bash Bunny
Review of Bash Bunny. My exprience with this hacking gadget, examples of BadUSB attacks, where to buy Bash Bunny and my plans for future use.
Looking Back at 2017 at PATRON-IT s.r.o.
Looking back at 2017. What interesting things have happened to us? And how has it influenced the further direction of our company PATRON-IT s.r.o.?
People Are the Foundation of Our Company
We are network administrator colleagues. What did we struggle with when recruiting? On what values we have finally built up PATRON-IT s.r.o. company?
How Did We Fight Microsoft Office 365 Support (Part 2/2): Microsoft Is Always Right
The customer is impatient, emails arrive late. We are still losing the fight with MS Office 365 support because we have failed to explain that the bug is at their side.
How Did We Fight Microsoft Office 365 Support (Part 1/2): The Nightmare Begins
Once, we've got a "cool" idea of unifying antispam for all customers on Microsoft Office 365 Exchange Online Protection. It was supposed to be a simple task.
Hyper-V vs. VMware: Why Did We Choose Hyper-V
Few questions can make "IT guys" so furious. Is Hyper-V or VMware better? We chose Hyper-V and there are 6 reasons why Hyper-V is better for us.
Data Backup – How to Not to Lose Data When Hacked (In Real Life)
Practical instructions for secure data backup. Technologies and practices, we trust. In the event of an attack, be assured that the backups will survive.
Data Backup - How to Not to Lose Data When Hacked (In Theory)
We often encounter inappropriately designed customer data backups. I'm happy to share with you how we are dealing with backing up the data.
Work Reports - a Miracle Cure That Came Just in Time
Work reports were a small revolution for us. They have allowed us to get more money for the same job while having a more satisfied customer.
Ransomware 2: to Pay the Ransom for Encrypted Data?
Broken server, encrypted data and backup as well. How to solve it? Is it worth to pay the ransom and get the data back?