Network Security: Tier Model and PAW
I still know most of the owners and bosses of the companies (companies that we take care of in PATRON-IT s.r.o.) personally. Although my positions are changing and I do not see them so often, the more responsible I feel for our work – we do our best (IT needs to work quickly, not restricting business while minimizing security risks) and efficiently (management cost not to be more expensive than what the company earns). But the more I know about computer security, the more headache I have. 🙂
I have been preparing for a few months already, to share some of my insights and impressions from computer security here on the blog. It took some time for me to figure out how to grasp it in order to put it clearly. I have also waited until I pass the EC-Council ECSA (EC-Council Certified Security Analyst) course. I think I’m ready to share the “little” I know now.
As I previously wrote in Looking back at 2017 at PATRON-IT s.r.o., last year we have improved a lot. This year I expect an equal shift – especially in “security”. Since the beginning of the year, we have already succeeded in replacing the password management system (Password Management 2: We Have Installed Remote Desktop Manager) that allows us to do things a lot safer without compromising efficiency. Since late last year, we have been working on deploying tiering and privileged access stations (almost done). I used the following Microsoft materials: Securing Privileged Access Reference Material and Privileged Access Workstations.
Tiering
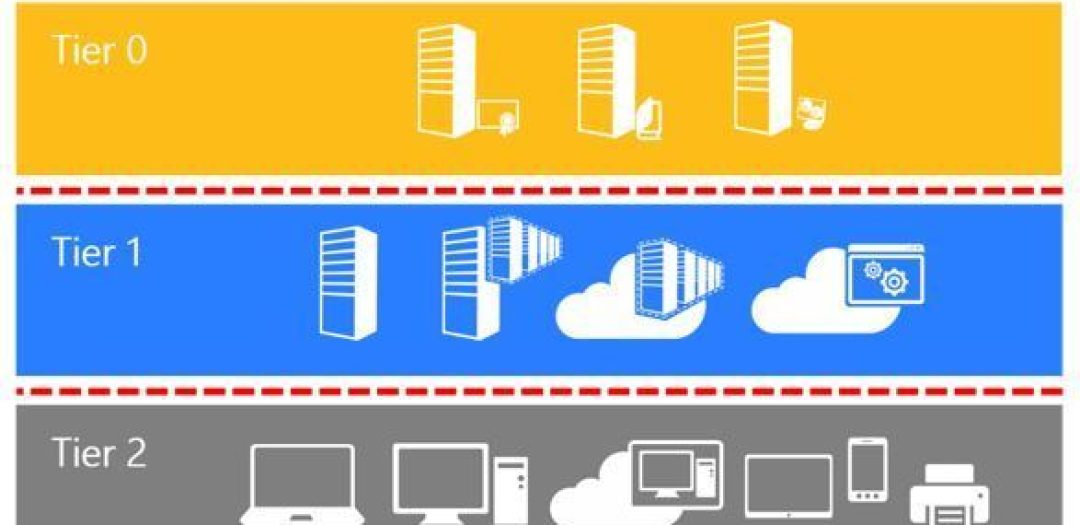
Since Microsoft’s model is based on the assumption that everything is in one “forest” (one AD domain), I have to adapt it. We have dozens of customers and everyone has their own forest and their “non-routable” networks. I made the result in the following illustration.

The rules are as follows:
- Devices and credentials are categorized into tiers (layers). Sorting is done according to the “importance” / “credibility” of the device. As a result, the compromisation of one-tier device/login data means compromising all layers below. It follows that the higher the tier (the higher the position in the picture), the higher the required security.
- The login data from each tier can only be entered on devices in a given tier or higher (eg, the RDP connection sends [according to the settings] user login and password to the destination station, ie it is as if you entered these credentials on this station).
- Lower-tier devices must NEVER manage a higher-level device and devices within the tier should not manage each other – if possible (eg from one member of the server I should log on to the other).
The picture shows that I have added a number of tiers (with negative numbering), that belong to our environment. Obviously, compromising our environment can compromise the environment of all customers. The worst case scenario.
The customer environment is isolated from one another, compromising one customer does not affect the environment of other customers.
For customers using virtualization, we divide Hyper-V guests (along with infrastructure management) from the rest of the network. I already wrote in Data Backup – Data Backup – How to Not to Lose Data When Hacked (In Real Life). And it is not possible to get in from the lower tiers (customer LAN).
In the right part of the picture, the arrows indicate the levels of access that we use in our company. Each one of us has only the rights and logins that he needs to do his job.
The blue rectangles in the image are censored. 🙂 I wondered whether I should keep the information, but in the end, I hid it. In their place is the classification of the major applications and systems we use, eg the central console, password management system. To know how much we have to protect and what would happen if they were broken.
Privileged Access Workstations (PAW)
Since the computer can be hacked through the browser and with no downloadable software from the Internet being completely safe (eg CCleaner case), we have decided on all of our remote-managed stations (that is, accessing from to customers and passwords), to introduce “strict” restrictions.
Of course, you can argue that there is no such thing with open source. But hand on the heart! Who of us goes through the source code? See OpenSSL Heartbleed bug. You may also think that I am paranoid. But compromising our PAWs can compromise all of our customers. I do not want to take the risk.
Sidenote: I wrote about Hacking Gadgets Hak5 (Bash Bunny and Packet Squirrel) early this year. It seems like I will have training ready soon (practical demonstration). I will at least share the slides with you. And If I’m not too ashamed, I’ll shoot a video.
We currently have deployed at PAW:
- APP whitelisting: it is allowed to only run the selected applications (it is not allowed to run anything that is from the internet, or brought via USB flash).
- Least privilege: nobody has administrator access to the PC (the password is known and the edits can be made by only a few of my colleagues).
- Encryption: there is a BitLocker on all PCs (protection against physical attacks).
- 2FA: 2FA is required to log into the station locally and remotely (we also have 2FA in all other systems).
- Antivirus: ESET with its own HIPS rules
- Other measures: Windows Security Baselines, automatic PC locking, NTLM disabled.
When we need to test a program, we do it in virtual machines (they do not have access to our LAN) that we have on our PAWs. When the test ends, we return the virtual back to the previous snapshot. The virtuals can never include confidential data.
Conclusion
Some people, when they know us, are surprised that we do not use work laptops. I admit that it’s sometimes funny to stand next to a rack and call my colleague at “HQ” to re-set or check something because you can not get to the gear in the rack. However, I find it better when the workstations stay at work and serve only for work. Colleagues then have their private laptops at home for personal purposes.
Now I’m curious again, how did you like the article? 🙂 Have you heard something surprising? Are you saying I’m wrong in something? Do not keep it for yourself and let me know, I really appreciate every feedback.
Are you interested in a specific topic that you need to address at work? Would you like me to write, how do we deal with it? Email me here or in a private message martin.haller@patron-it.cz.
Together we will do IT better. As best we can! ✌ 😊











Discussion