Posts
Infostealers reveal everything: your logins, identity, and even your home address.
Talk: Microsoft Entra ID – Defense
Our recommendations for setting up the Entra ID tenant, conditional access policies, what to monitor, and with which tools to audit Entra ID.
Talk: Microsoft Entra ID – Lateral Movement & PersistenceTalk:
After a successful phishing attempt, attackers aim to elevate their privileges and maintain access to the compromised Entra ID environment for as long as possible.
Talk: Microsoft Entra ID – Attack Surface
Technical training on how attackers gain access to Office 365 / Microsoft Entra ID.
Moving to Azure Active Directory
I want to strengthen the security level of our environment, and I think that AAD can help us with that for the following reasons.
Our Insights from Security Audits in Companies
A list of frequently recurring basic errors that we encountered during audits.
Why I want to deploy EDR to all customers
What is EDR? What does it offer? Why do I think it is great technology for any company dealing with IT security.
Overblown Expectations from Security Technologies
Four frequent and unrealistic expectations from SIEM and sandbox I often encounter.
Cutting Down Trees in Our Forest
Last week, hackers managed to break in and encrypt one server of our customer 😤.
The Myth of Cybersecurity Training for Employees
In other words, why employee training is not what most companies need.
Attack on IT companies: Kaseya VSA
Thanks to the cloud and globalization, we are connected more than we think. The mistake of the Kaseya producer seriously damaged the customers and customers of their customers.
Insights from interventions during a ransomware attack
Bitcoin in retreat, rising ransom and fading honesty. Our new experience from the world of ransomware.
How to start a career in cybersecurity?
Tips for starting a career in cybersecurity. Distilled experiences of my friends and me. Courses, websites, certifications, duration.
How Difficult is to Detect a Data Leak
Data leak? After a hacker attack, companies usually ensure the public that no personal data has been leaked. But, how do they know it?
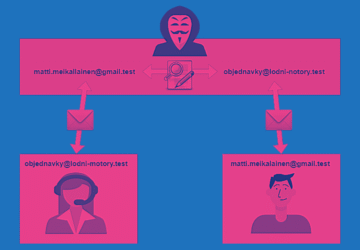
Business E-mail Compromise: Leading Cyberattacks
Business E-mail Compromise cyber attacks type Counterfeiting emails, identity theft aimed at making money. How do the BEC attacks work?
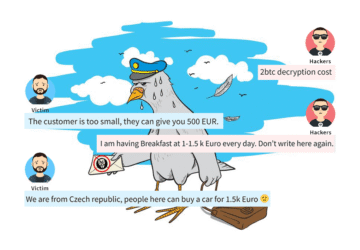
What Does Ransom Negotiation Look Like
Demonstration of real communication between ransomware victims and hackers. Ransom negotiation, contract prices, pro-customer approach and non-stop support.
How Could Hackers Attack Vltava Basin? OSINT Research
How to use publicly available information and find a security flaw in the network? OSINT method and Vltava Basin hack case study.
How To Recover a Network After a Ransomware Attack
How to restore a corporate computer network after a ransomware attack? What to start with? I´m sharing the (hard-earned) experience so that you can restore operations as soon as possible.
Why Using VPN to Secure RDP Will Not Stop Hackers
Wondering how to increase RDP (remote desktop) security? Let me tell you how hackers most often hack RDPs and why VPN won't change anything about it.
EPYC Case Study: Servery DELL 15. AMD Gen Once Again
We have been testing the Dell PowerEdge R7515 server with a 2nd generation AMD EPYC processor. How did the AMD EPYC do vs. Intel at 4 of our customers?