Posts
Ransomware actors have a new trick. None of backup solutions can mitigate it. They are threatening to release all the stolen information.
What hackers can do in your network
Companies end up without data or backups after a ransomware attack because they underestimate the skills of hackers. Learn what a hacker can do within your network and how to improve security.
Security insights: Laptop webcam hack
Did you tape your webcam because you're afraid of hackers? The video shows how easy it is to hack a laptop webcam. Do you know how to defend getting hacked?
HackerFest 2019 Workshop Sample
We have made one Linux virtual server available for you to hack from the comfort of your home just after the HackerFest 2019. Go on!
Are Updates Really So Important?
To update or not to update? Updates are a neverending topic. In this article, you will learn why to update and how often.
Windows 7 and Windows Server 2008 support ends. What to do?
Windows 7 and Windows Server 2008 R2 support will end on January 14, 2020. Upgrades are fully underway. What do we replace Windows with?
My view of IT certification MCSE, CCNP, ECSA, CHFI, OSCP
Are you considering where to get certified? I bring my insight into IT certification MCSE, CCNP, ECSA, CHFI, OSCP. Training, exam, practical benefits, price.
OSCP: Offensive Security Certified Professional
Over 60 servers hacked, 5 months of life and 1 exam. My path to OSCP certification: Offensive Security Certified Professional.
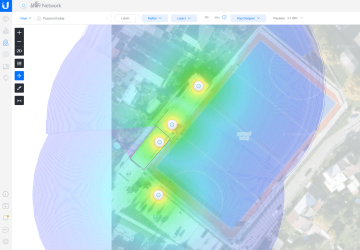
Ubiquiti UniFi Case Study: Hradec Králové Stadium Connectivity
We needed to cover a stadium for 500 participants cheaply and without downtime. We chose AP Ubiquiti UniFi. UniFi controller review and conclusion.
Security Insights: How to Get Hacked by a RDP Server
Compromised computer or stolen data? Watch a video on how to get hacked by a RDP server. And then read how to defend against this attack.
TeamViewer: 4-Year User Review (Part 2/2)
TeamViewer and its imperfections. What don't we like after 4 years of use? And how do we set TeamViewer up to be as safe as possible?
TeamViewer: 4-Year User Review (Part 1/2)
TeamViewer is our remote user support tool. We can handle over 270 connections a week. What do we like about TeamViewer? And why did we buy it?
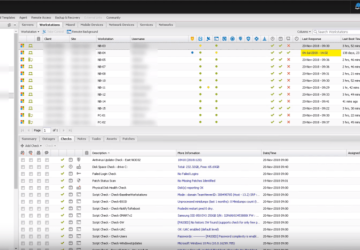
Monitoring system video: How We Oversee 2000+ Network Devices
The monitoring system, thanks to which we have our networks in order and a constant overview of their health. Practical video directly from the production environment.
Barcamp HK 2018 - Danger in The Name of USB
How easy is it to hack a computer? Video recording from my Barcamp lecture in Hradec Králové. I'll tell you about the danger that comes through USB.
Ubiquiti UniFi and Fortinet Security Fabric
Ubiquiti UniFi and Fortinet Security Fabric help us manage larger networks, with more security and less effort. Little revolution in network management.
HackerFest 2018 and what we couldn´t fit into the lecture
I will share with you the USB hacks we and William Ischanoe had taken a bite of at HackerFest, but there was no time to go in depth.
Why Is Server Slow: Momentary Problems
hy is the server slow? Article about solving performance problems, measuring performance, finding bottlenecks, and designing new servers.
How We Were Able to Lose Closed Deal
So far I have only shared our successes. We fail as well, occasionally. I would like to share a fail with you today and what lessons we have learned.
Honeypot: Efficient and Cheap Way to Detect LAN Attacks
What honeypot can do? And what does an ideal LAN attack detection system look like? Practical insights how honeypot detects unwanted activity in the network.
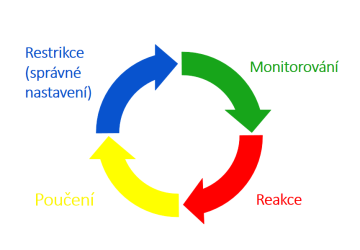
IT Security: Security Life Cycle
My practical insight into IT security and security life cycle. Everyone deals with restrictions, but what about monitoring, reactions, and lessons learned?