What Does Ransom Negotiation Look Like
I devoted the previous article to the OSINT method – how to work with information that is publicly available online. Using the available info, we found one critical vulnerability in Vltava Basin, which could have been the entry point for hackers into their network. The article was subsequently “republished” at Lupa.cz [CZ] and I have received positive feedback from many of you. Thank you all very much for that! I will continue to try to bring you fresh information and practical procedures.
I received a recording of communication between ransomware victims and attackers last week. As I worked on it, I realized that a lot had been written about ransomware, but not as far as much about communicating with attackers. 🙂 Basically, I saw but two articles that show the communication („How to Haggle With Your Hacker“ and unfortunately, I did not manage to find the second article). I have decided to share the record of the ransom negotiations with you. Including observations that I found interesting in communication with hackers.
I understand that communicating with attackers and paying the ransom is beyond that imaginary line for some people. But let’s leave the moral dimension aside now, please. The situation has already happened. Let’s use communication to expand our knowledge of ransomware “business“.
Ransom Communication
1. 2. 2020 20:32
Hi guys!
good work!! My name is ****. I was asked to upgrade “security” for a small customer you hacked (all-in-one server ). They don’t want to recover the data, as they have backup from 28th January.
I suggested them to pay, if the price is reasonable to save some time. They’ve refused as they don’t want to support terrorists.
What is the price of your time to help?
2. 2. 2020 23:18
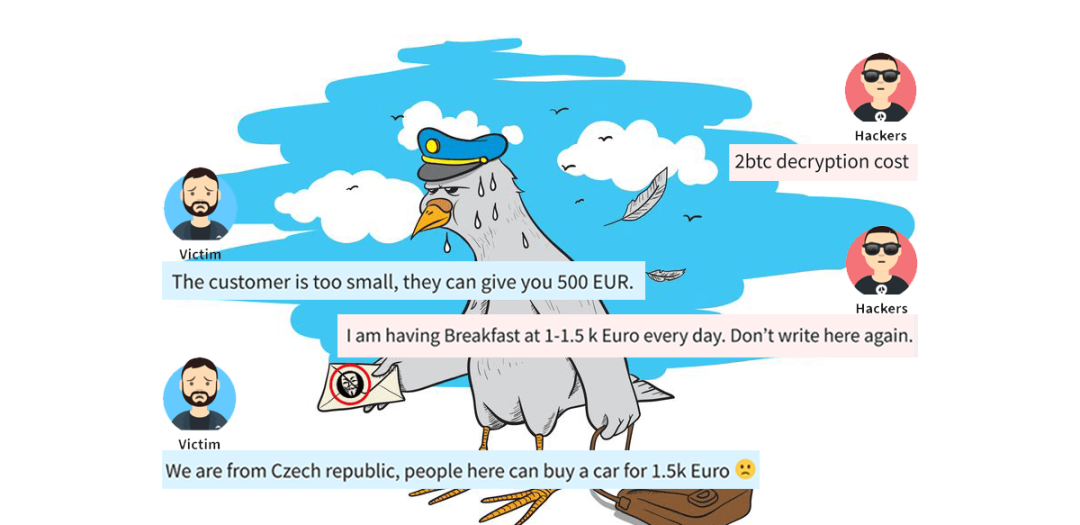
2btc decryption cost
2. 2. 2020 0:02
The customer is too small, they can give you 500 EUR.
They don’t really need the data. The backup they have is quite fresh
2. 2. 2020 0:06
I am having Breakfast at 1-1.5 k Euro every day. Don’t write here again.
2. 2. 2020 0:18
We are from Czech republic, people here can buy a car for 1.5k Euro 🙁
So they can buy a breakfast for you then. 1000 EUR? They should be able to pay.
I’m trying to help you to get at least something, you had some work with the hack.
2. 2. 2020 13:41
Hi there,
if the recovery will be available today, they can give you 0,5 btc
Last call, or they will use 10 days old data from backup and continue their work. At that point, data integrity will be changed and old server data will be valueless.
If you want money, respond fast.
2. 2. 2020 13:51
Ok 0.5 Btc deal
Our wallet ****
How much time do you need to complete the payment?
2. 2. 2020 14:27
We have responded to you. We are ready for a deal. Waiting for payment.
2. 2. 2020 14:57
We waiting for money transfer to coinbase, need about 60 min.
Can I ask you to decrypt 3 files as a proof for the owner?
Thanks
2. 2. 2020 17:29
Sorry, I was waiting for my boss to pick up the decrypted files
2. 2. 2020 17:36
https://dropmefiles.com/****
password ****
Here is a link for decrypted samples
2. 2. 2020 19:34
How much time do you need to complete the payment?
2. 2. 2020 20:11
Unfortunately the deal was canceled by the owner. We have money prepared in btc for you, but the owner decided to use 10 days old backup after they tested its integrity as its cheaper to pay people to rework this 10 days.
Sorry for that, I am also not happy as we failed in negotiation with you
2. 2. 2020 20:13
Offer them a discount. we are ready for the amount of 0.3 BTC
2. 2. 2020 20:27
To be honest, they would pay, but they want guarantee. If they pay, they wanto to be 100% sure the data will be back, they have no insurance etc. They had similar issue in the past, they payed and nothing happened.
Also some technical problems can occure, I’m not sure what their IT tried on server before we came.
And I cannot guarantee that by my name.
2. 2. 2020 20:29
We’ve already shown you the decrypted files. We can decipher a few more as a guarantee. You can be sure that the files will be decrypted in any case. We are waiting for your decision.
2. 2. 2020 20:45
I understand, but they want us to take the risk. Look, we already know a few of hacking groups and we have some kind of trust between us. We help them, they help us.
But usually we negotiate the deal, customer take the risk and we know each other since.
In this case they don’t want to take the risk, and you are new for us.
2. 2. 2020 20:51
New? AHAH We work since 2013
Ok good luck. We will delete their key tomorrow morning
2. 2. 2020 21:00
Haha 2013 sorry than 🙂
Send me the decryptor and you have my word that I will pay 0,3 BTC to you if it will work. I have 3 people on place right now. It could be fast
2. 2. 2020 22:48
If I will take the risk and trust you, can you give your word that you will help?
2. 2. 2020 23:03
Man what do you want for me?
We sent you the transcribed samples as a guarantee, it’s not enough for you. What else do you want from us?
You refused the deal. Tomorrow we will delete the key
2. 2. 2020 23:14
I’m trying to make money for you!
Owner refused to pay, as he doesn’t believe the recovery will be successful
If I will trust you and send you the money it is my risk to help both sides. So I want your gentleman’s word that when I send 0,3 BTC, you will decrypt the data.
2. 2. 2020 23:23
The price will be 0.5 BTC. we will not give you any more discounts. Either pay 0.5 BTC and get your decoder, or don’t email us anymore.
2. 2. 2020 23:35
I just tried to help you, they already decided not to pay and recover the old data. It is my initiative to send money and recover the data. But I don’t care, it is not my data.
2. 2. 2020 23:35
I’m going to sleep for 2 hours. Pay for it, I’ll give you a decoder. when I get back. Wallet **
and read about Matrix Ransomware on the forums-all our customers get the decoder after payment. We have 20-30 payments a day, and we value our reputation.
2. 2. 2020 23:40
I can give you 0,3 BTC but I need to have decoder now, my people are there and they have to make it work until morning. We promised the network will be functional in the morning.
2. 2. 2020 23:52
You yourself offered a price of 0.5 Bitcoin. we will meet you halfway. 0.4 BTC now, and I will issue you a decoder within 5 minutes of receiving the payment. Decoding will take 30-40 minutes
3. 2. 2020 0:00
They considered 0,5 BTC and then they refuse it and ask us to recover old data. Please, take 0,3 and we can go sleep. I can not go against their decision they already made. I really have nothing from this situation, we are paid hourly.
3. 2. 2020 0:10
I’m tired of you. I already gave you a great price, what the fuck are you bidding for? 0.4 this is my last offer. You have 5 minutes to pay. And don’t lie about hourly pay, I know hundreds of dealers like you and I know how you work.
3. 2. 2020 0:16
I am not a fucking dealer :(. We are repairing what IT guy did. Ok. I will send 0,4
3. 2. 2020 0:22
0,4 BTC has been send, is it ok ?
3. 2. 2020 0:22
ok see payment
please wait 5 min
3. 2. 2020 0:23
Please send us 1-2 encrypted samples once more
we will generate your key
3. 2. 2020 0:26
Could be those you have already seen? (attached)
3. 2. 2020 0:30
https://dropmefiles.com/****
Archive password: ****
(if you will not be able to unpack the archive please install Winrar)
Here is your PAID Decryption Tool and Decryption KEY.
This decryption key is based on files which you sent us for free test decryption.
Decryption tool is tested on files which you sent us for free test decryption and work correctly!
Unzip decrypt tool in some folder, for example: C:\1
Run dec.exe as administrator with right mouse click.
Wait while file scan process will be finished. (scan process can be long)
Write full path to .SEK key and press enter, for example C:\1\XXXXXXXXXXXXX.SEK
Decrypt process will start…
If you want to decrypt some folder or local disk, you can:
drag and drop this folder or local disk to dec.exe by left mouse button.
wait file scan finished.
Enter full path to .Sek key, example c:\dec\XXXXXXXX.sek
Decrypt process will start.
If you have dec fail errors during decryption process it means
that you have additional keys generated by our software.
Additional decryption keys are extra chargeable.
If you will need help please write us!
3. 2. 2020 0:33
Thank you, we will test it.
Last question. There was 1 server and 1 PC encrypted, but PC has another ID , will works for both or should I send samples also from PC ?
3. 2. 2020 0:34
No. You must send us samples from PC too if you need the second key.
It wiil be free for you
3. 2. 2020 0:36
Thanks. (attached)
3. 2. 2020 0:41
My boss just went to bed. we will give you the key for the PC in the morning, there are a few files, you will have time to decrypt everything before the start of the working day. We have a difference of 3 hours with you, so we will send the key when your business day has not started yet.
Waiting for the files
3. 2. 2020 8:07
Hi guys, we have just finished the decryption process.
Thanks for the decryption tool. We have noticed that some of files have not been decrypted – they stayed in encrypted state. We didn’t notice any error message during the decryption process.
You can see the files in attachements.
Could you help us with that please?
3. 2. 2020 9:04
https://dropmefiles.com/****
What Do I Find Interesting Regarding The Ransom Communication
My observations on communicating with hackers …
The original and final price of the ransom
Negotiating a ransom is reminiscent of bargaining at a Turkish bazaar. The attackers demanded 2 BTC (at that time about 440,000 CZK) at the beginning. The final price paid by the victim was 0.4 BTC (approx. CZK 88,000 CZK), which is just about 20% of the original amount. Getting an 80% discount is, in my experience, a very good performance. What discounts can be achieved depends on the customer’s willingness to take risks (there is a risk that you will annoy/offend the attacker and the communication would stop) and the time urgency to get the data back (it depends whether you need it within an hour or a week).
Negotiation Strategies
It’s like playing poker. Each side knows its “cards”, tries to keep the “poker face” and guess the “cards” of its opponent.
- The victim knows the price of its data (how much it is willing to pay) and knows the seriousness of the situation (whether there are current/historical backups, how much data is irretrievably lost). However, the victim needs to play a game that nothing really happened and that most of the data can be restored from the backup. So there are just a few non-critical documents encrypted, but it would be nice to have them back. At the same time, the victim tries to estimate the lowest ransom amount the attackers would be willing to accept but tries not to offend them enough to refuse further negotiations.
- The attackers know who was attacked, which was deleted/encrypted in the victim’s network, and what is the lowest price at which they will release the data. However, they need to estimate how bad the victim´s situation is (whether any backups survived or not) and what value the data has. They must “price” the ransom on that basis. The most willingly paying companies are the ones that find themselves with no data. Partial backups are already lowering their likelihood and those that have a backup of all data are the least likely to pay. They uncompromisingly face the victim, creating time ultimatums with a risk that the victim will never see the data.
- The negotiation is much easier from the third person view of an uninterested person rather than from the side of a company that might end its existence. The victim’s initial counter-offer of EUR 500 (less than 3% of the requested amount) was bold, but in my opinion, it helped to significantly reduce the ransom (kind of “price counterpart”). The attackers demonstratively paused for half a day. The victim “did not push” the case, making it clear to the attackers that the data was not really critical, which led to a significant ransom discount.
- The negotiation reminded me of a „Never Split The Difference“ book by Chriss Voss. If you are interested in the psychology of negotiation, I highly recommend it (at the same time you will support one great publishing house, especially in these hard times).
Hackers Like To Brag
One would expect hackers to remain “anonymous.” However, they seem to be proud and happy to boast about their history and the name they have earned. In communication, they boast that they are the Matrix group, have been working since 2013, and receive 20-30 payments a day. Of course, it remains to be discussed whether this information is true. From our experience in other cases, it is common for hackers to brag about their name – they try to “guarantee” the victim that the data will really be provided once the payment is through using their reputation as leverage.
Hackers Are Organized
It can be seen that more people take turns in communication. Two at least. One get´s called boss, who, unlike the first person, has access to the decryption keys. There are hierarchies and different authorizations pointing towards “professionalization“.
Customer Service
Most of the communication took place during the weekend, day, and night. The attackers mentioned that they were in GMT+4 and the answers were even received in a matter of minutes. Likewise, hackers were willing to help decrypt files that their program did not decrypt.
This shows that they really care about “good” reputation. It is the only thing, based upon which the victims are willing to risk paying the ransom, even before the data is decrypted. Unlike the “legal” business, there is no exchange through “lawyer/notary custody”. 🙂
Communication And Payment
Few more notes from our experience:
- The communication is in English and via e-mail. The attackers leave a “ransomnote” (blackmail letter) in the victim’s network with instructions on how to contact them (the attackers are currently also creating self-service “stores”). A letter oftentimes mentions multiple email addresses. This is in case one of the e-mail boxes is blocked (eg by the police). The attackers we encountered most often use the protonmail.com and cock.li email servers.
- A ransom is usually requested in Bitcoins. It´s their go-to coin due to the irrevocability of payments, the prevalence of cryptocurrency, and “pseudo-anonymity”. However, it is possible that due to higher anonymity, other cryptocurrencies will be preferred. For example ransomware group Sodinokibi/REvil started to use Monero.
- Ransom negotiation is not always that long as in this case. It sometimes takes only a few emails. Especially when the customer is really in a hurry to recover the system and the ransom is “badly” (meaning low) priced by the attackers. Personally, however, I would recommend to “cry” a little before the ransom is paid. So that the attacker would not feel like the victim could pay more and would try to increase the price.
Conclusion
In conclusion, let me remind you of the very important: Paying a ransom supports the ransomware “business” and leads to other compromised companies. If it is possible to restore data from backups, I recommend doing so and avoid paying the ransom.
If you have noticed any other interesting things in communication, please share more in the comments. I would also appreciate any feedback or ideas. 🙂
If you are interested in the ransomware topic, have a look at my previous articles:
- „How To Restore A Network After A Ransomware Attack“ – how to restore a corporate network after a ransomware attack? Where to start? I share the (hard-earned) experience so that you can resume operations as soon as possible.
- „How Hackers Attack Companies Through Their IT Providers“ – It doesn’t matter how much you invest in IT security, as long as your provider slacks. Beware of hacker attacks through IT providers.
- „ Hackers Came Up With a New Trick. They Learned To Improve Their Blackmailing With Ransomware“ – Not even a good backup would resolve the new ransomware scam. Hackers blackmail victims by disclosing their sensitive data if they do not pay up.
- „What Hackers Can Do In Your Network“ – companies end up with no data nor backups after a ransomware attack because they underestimate the hackers´ abilities. Learn what a hacker can do on your network and improve your security.












Discussion