The Myth of Cybersecurity Training for Employees
Today’s topic might be somewhat controversial, as I’ll dispute the mainstream opinion on cybersecurity training for employees—regular computer users. Personally, I feel that the prevailing opinion is that:
Untrained users are the main cause of significant cyber incidents. Thus, we should educate them, even if they are not interested!
I disagree. I believe that employees… or rather specific employees, are the problem, but not the ones typically thought of. The greatest responsibility for security rests on the IT departments’ employees. We, the administrators.
Okay, we’ve got a somewhat tabloid-style introduction out of the way; now, let’s examine my arguments.
Why Cybersecurity Training for Employees Isn’t What Most Companies Need
Educating employees on cybersecurity is, of course, a legitimate measure. However, the benefit/cost ratio of this measure is not exactly splendid.
Not All Attacks are Conducted Through Employees
The media mainly talk about “phishing emails” that lure login details from users or execute infected attachments. Rarely is there talk about companies attacked through unpatched vulnerabilities, poor configuration, or weak administrative account passwords. However, these initial vectors form a significant part (I once again refer to the latest chart from Coveware).
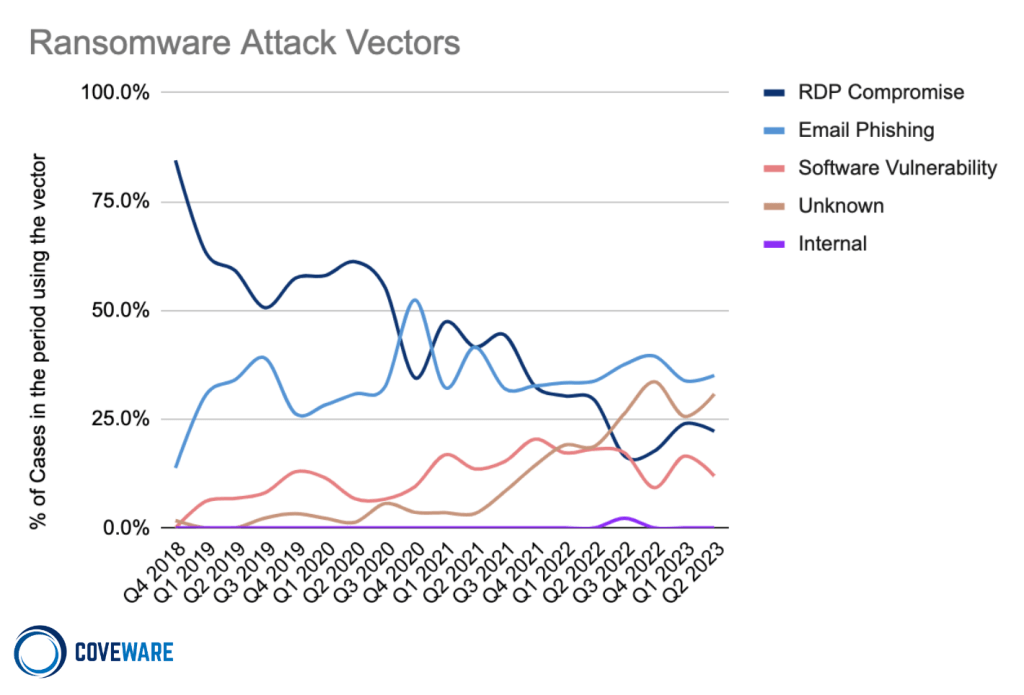
Intrusion Vectors to the Network (source: https://www.coveware.com/blog/2023/7/21/ransom-monetization-rates-fall-to-record-low-despite-jump-in-average-ransom-payments).
I would like to add some rarely mentioned aspects:
- Email Phishing – Even when attackers deceive users, they haven’t won yet. They only have user access, insufficient to delete backups, encrypt all data, or stop servers. The attack continues after gaining user rights. This time, attackers face administrators, and only after “defeating” them is the network lost.
- Vulnerabilities, Weak Admin Accounts, Poor Configuration – In this case, regular employees are not involved; it’s all about the administrators. These attacks are usually very fast since attackers have unrestricted network access from the beginning.
As you can see, not all attacks come through regular users. However, IT administrators play a role in every one of them. Therefore, we should mainly train administrators.
Cyber Attacks are Sophisticated, Hard to Detect
Sometimes, even people in the IT field fall for well-executed “social engineering” (e.g. phishing) tactics, sometimes those directly from IT security. I wonder, how can we have the power to train regular (non-IT) users when even the experts aren’t foolproof?
Of course, nothing is black and white, and there will probably be the classic Pareto principle at play. 😊 Through proper training, we can educate employees to recognize 80% of attacks. And we simply accept the undetected 20% (they must be covered by other measures).
However, during training, we must not forget that employees are not students, whose main job is to learn new things. Employees have their work obligations, personal sorrows and joys, and different approaches to computing technology.
I believe that as IT administrators, we should mainly create a “safe and simple” environment for users where they can’t mess anything up.
There are too many employees for none of them to make a mistake.
Once a company has several hundred employees, it’s hard to train everyone – there’s always someone sick, on vacation, on a business trip, doesn’t have time, or is newly hired. The more you rely on training your employees (you have fewer other defensive measures), the harder it is to keep everyone “trained.” Besides, as I mentioned earlier, not all attacks are conducted through them. 😉
But where do you find significantly fewer people? In your IT department! Yet, all attacks pass through (and they play a role in) them.
For these reasons, I believe that it’s cheaper to train your 3 IT employees than their 300 colleagues from other departments. 😊
What’s the way forward?
My opinion is, if we want to increase security, we should primarily invest in our IT employees. They should subsequently create a safe and simple environment for their users.
Sometimes, technology appears that can increase both security and user comfort. An example I often give is fingerprint/face scanners on mobiles. Before, we either had to use PINs or draw patterns. This was inconvenient, and someone looking over your shoulder just once could catch your PIN. Now, with fingerprint scanners, 👆🏼 we all have secured (and encrypted) phones without any inconvenience. This is the way forward, in my opinion.
Of course, devising suitable security solutions is not easy, but I believe it’s possible. 😊 Here are two insights that can help many people:
- Macro Disabling: Many phishing emails involve coercing the user to run macros. Many companies try to tackle this threat with employee training, antispam, antivirus, and sandboxing. However, from my experience, most companies don’t need macros at all (or just a few employees in the company do). I say, why not just disable them (or limit them to digitally signed macros)? This solves the macro problem and it’s free. 👍🏼
- Application Control: determining which applications users can run and which they can’t. Most users need only a limited number of applications. So why not allow them to run only these and prohibit the rest? You won’t have to deal with users using unapproved software or accidentally running malware (because they simply can’t). Application control can be implemented through SRP (Software Restriction Policies), AppLocker, or often your antivirus can manage it.
Conclusion
What do you think? Did I convince you, or do you have any “BUTs”? I’ll be glad if you share your opinion.
May your networks stay secure,
Martin













Discussion