Insights from interventions during a ransomware attack
Thanks to the ransomware, we’ve been overloaded for the last few months. We helped 8 companies get back on their feet after a ransomware attack. We either provided them a consultation over the phone, helped remotely, or went straight to their companies.
The interventions on the spot are usually the most demanding. These are mostly “definite”—everything encrypted, including backups. And so, we fight for the existence of long-established companies and their employees. Intervention means a lot of stress for most involved and a work/sleep regime.
The last few interventions even took us 2 weeks. And additional security will be worked on for next more months.
Unfortunately, sometimes it happens that we cannot help some companies due to capacity reasons (e.g., we already help other companies). And then I am professionally and humanly sorry for such situations.🙁
As you can see, we haven’t been bored since the beginning of the year. We have a lot of new experiences to share. At the same time, a new report from Coveware was released (1Q2021 – “Ransomware Attack Vectors Shift as New Software Vulnerability Exploits Abound“). So, let’s see what’s new.
Bitcoin in retreat?
We have the first case in which the attackers ultimately refused to pay the ransom in Bitcoin and instead demanded Monero. The transition from Bitcoin to other currencies has been talked/written about for several years (e.g., “Ransomware: Why the crooks are ditching bitcoin and where they are going next“, “Sodinokibi Crypto Ransomware Switches from Bitcoin to Monero to Hide Money Trail“), but this is the first time for us that the attackers did not want to accept Bitcoin.
Monero provides attackers with greater anonymity than Bitcoin. I believe that is the reason why they are switching to this currency. However, in addition to the police, this complicates the situation for companies that would need to buy back their data. 🤔

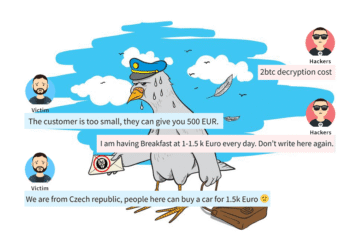
Bargaining like at a Turkish bazaar
Already in previous articles, I presented that ransom values are like prices in a Turkish bazaar. The price depends on “who” and “how”, he asks. The cost can then be moved – both down and, unfortunately, up.🙁 The whole topic would take a separate article.
However, over time, the amount that the attackers say on the first attempt begins to change. About 5 years ago, it was units up to tens of thousands of crowns. Then it became hundreds of thousands, and now it is units up to tens of millions of crowns 🙁 (much depends on the size and type of attacked company).
Coveware states in its report that, according to their data, the standard (median) ransom payment was $ 78,398 (approximately CZK 1.6M). However, I must note here that they probably mean the paid amount. While I state the requested amounts (i.e., before the negotiation).

The honesty is disappearing
Before the attackers encrypt the victim, they stole part of the data. Subsequent blackmail then includes the threat of publishing the data on the Internet if the victim does not pay. According to Coveware, this happens in 77% of attacks (which we can confirm). Unfortunately, even if the victim pays, the stolen data simply will not disappear. Attackers sometimes blackmail victims repeatedly. And often, stolen data will still escape. It is, therefore, better not to play this game with the attackers and immediately start preparing for the release of the data.
Likewise, it is sometimes the case that attackers supply only part of the decryption keys. They will ask for more money for the delivery of others.
They will be happy to return to the network
If the company is attacked by attackers, it is necessary to take care of the recovery. Especially if you decide not to pay the attackers (because you have backups). That’s primarily annoying for them. And if they have a backdoor left in a network (or an uncorrected “initial attack vector”), they will return and do the “work” for the second time properly (a few such cases we helped with).
However, even if you pay, you still need to do the restoration properly. Coveware writes (if I understood correctly) that the ransomware of the “Conti” group is soon re-attacked by the victim, even though they have paid a ransom
The companies will never see some of the data again
Even if the victim pays and gets a decryptor, not all data can always be recovered. Unfortunately, we already have personal experience because sometimes some data is corrupted during encryption and therefore non-recoverable.🙁
From their experience, Coveware writes the following (free translation, these are exceptional errors rather than a problem with the whole “family” of ransomware):
- Lockbit: technical errors in the ransomware caused data loss.
- Sodinokibi: due to a technical issue, the attackers could not locate the decryption keys, and the victims could not decrypt their data.
- BlackKingdom: when trying to encrypt all Exchange servers, they made a mistake and caused data loss (instead of encrypting it).
Outsourcing and specialization
Cybercrime is not about individuals but increasingly better-organized groups, with each group focusing on what works best for them. In the field of ransomware, we have:
- Ransomware developer (“founder”): theydevelop ransomware (encryption program) and other “operational” tools (shaming web, chat, payment gateways). They then provide everything for the “commission” to the attacking groups (RaaS – Ransomware as a Service). This whole enterprise (developers and attacking groups) is called after the name of the ransomware. For example, Sodinokibi, Ryuk, Conti, Avaddon, CryLocker.
- Attacking groups (aka “affiliate “): they attack corporate networks, steal data and then deploy selected ransomware (see above).
- Access vendor: some groups specialize only in obtaining access data and backdoors to companies. They do not attack them themselves but sell these approaches to “attacking groups”.
And new (which I would not have thought of before), we also have organizations that provide “chat and negotiation with victims”. In essence, the attackers (probably have a lot of work to do or don’t enjoy it) outsourced negotiations to other entities. Coveware mentions this strategy in ransomware groups from the “Conti” family. However, I would say that we have encountered this strategy with other ransomware families too.
They use the same tools as we do
Many administrators think that antivirus will save them from hackers. They also believe that if they scan a PC with antivirus and it doesn’t find anything, the station is clean.
Yes, hackers use tools that antivirus can detect (e.g., Cobalt strike, ransomware itself, Mimikatz). However, they also use devices that we administrators use, and they do not detect antivirus (RDP, TeamViewer, AnyDesk, Network scanner, web browser).
Actually, we register AnyDesk during the attacks more often. It serves as a backdoor for them (antivirus does not detect it, and the router does not block it), which allows them to work efficiently (basically as RDP, just without the need for port forwarding).
It is similar to the knowledge of access data. No antivirus will reveal that attackers know the domain administrator’s password. However, its ability allows attackers to control the entire network.
In the photo below, you will find a list of tools that hackers used in one attack to give you a better idea. For example, “Netscan” is a legitimate network scanning tool commonly used by administrators. It is not even freeware, but relatively expensive SW (attackers, of course, steal it).

Intersection vectors
From Coveware observations, in Q1 2021, the most common primary intrusion vector was again the RDP service, followed by phishing. This time, however, the ratio of network intrusions due to software bugs also grew.
The hacking of companies through the exploitation of vulnerabilities strikes me as the most technically interesting. We have been dealing with one of these recently, and I must write that it was very nicely done. The attackers are improving very quickly.
To prevent hacking through a software vulnerability, it is “enough” to update in time. However, it turns out that larger companies often do not have an overview of what SW and HW they use, and therefore some updates are overlooked.

Conclusion
If you have any other observations that were not mentioned in the article, I will be delighted if you share them in the comments. My goal is to help each other and secure our networks from attackers.
If you happen to have a disaster, try to contact me (see the email in the signature). Over the years, we have managed to find a way to recover some data under certain circumstances without paying a ransom. In this case, please email me the ransomware name, the incident date, the type and amount of encrypted data.
Keep your networks secure,
Martin












Discussion